 Zones
tab
Zones
tab  Zones
tab
Zones
tab
|
Click the numbers to learn about specific controls, or read an introduction. |
The Zones tab contains the traffic sources (computers, networks, or sites) you have added to the Trusted Zone or Blocked Zone. It also contains any networks that ZoneAlarm Pro has detected. Use this tab to:
Tip If you are using a single, non-networked PC, you don't need to use this tab. The traffic source list displays only your ISP's network, which should be in the Internet Zone.
The list displays the traffic sources and the Zones they belong
to. You can sort the list by any field by clicking the column header. The arrow
( ![]() ) next to the header name indicates the sort order. Click the same header again
to reverse the sort order.
) next to the header name indicates the sort order. Click the same header again
to reverse the sort order.
|
Field |
Information |
|
Name |
The name you assigned to this computer, site, or network |
|
IP Address/Site |
The IP address or host name of the traffic source |
|
Entry Type |
The type of traffic source this is: Network, Host, IP, Site, or Subnet |
|
Zone |
The Zone the traffic source is assigned to: Internet, Trusted, or Blocked. |
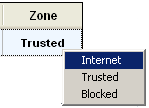 |
To change the Zone of a traffic source, left-click click in the Zones column for the source, then select from the shortcut menu. |
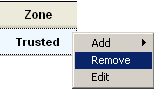 |
To add, remove, or edit a traffic source, right-click in the Zones column for the source, then select from the shortcut menu. |
![]() Tip
You must click the Apply button to save your changes.
Tip
You must click the Apply button to save your changes.
The entry detail window displays information about the traffic source currently selected in the traffic source list. The fields are the same as those in the traffic source list.
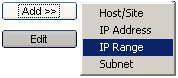 To
add a traffic source to the list, click the Add button and select the
type of traffic source you want to add from the shortcut menu. The Add
dialog box will appear.
To
add a traffic source to the list, click the Add button and select the
type of traffic source you want to add from the shortcut menu. The Add
dialog box will appear.
To change the Zone or any other information about a traffic source already in the list, select the traffic source, then click the Edit button. The Edit dialog box opens.
To remove a traffic source from the list, select it, then click the Remove button.
To save any changes you have made in this tab, click the Apply button.

Use the Add and Edit dialogs to provide or change the Zone, address, and description for a traffic source. The fields available will vary depending on the type of source involved (host/site, IP address, IP range, or subnet).
Access the Edit dialog by selecting a traffic source from the list, and clicking the Edit button.
Access the Add dialog by clicking the Add button.
Trusted Zone
The Trusted Zone contains computers you trust want to share resources with.
For example, if you have three home PCs that are linked together in an Ethernet network, you can put each individual computer or the entire network adapter subnet in the ZoneAlarm Pro Trusted Zone. The Trusted Zone's default medium security settings enable you to safely share files, printers, and other resources over the home network. Hackers are confined to the Internet Zone, where high security settings keep you safe.
Blocked Zone
The Blocked Zone contains computers you want no contact with. ZoneAlarm Pro
prevents any communication between your computer and the machines in this Zone.
Internet Zone
The Internet Zone contains all the computers in the world—except those
you have added to the Trusted Zone or Blocked Zone.
ZoneAlarm Pro applies the strictest security to the Internet Zone, keeping you safe from hackers. Meanwhile, the medium security settings of the Trusted Zone enable you to communicate easily with the computers or networks you know and trust—for example, your home network PCs, or your business network.